BitVM2 vs ColliderVM: The Layman's Guide
Breaking down the two paths towards trust-minimized computation on Bitcoin.
Bitcoin’s scripting environment is intentionally restrictive — designed more for safety and simplicity than expressive programmability. This design limits the native ability to perform stateful or Turing-complete computations, which are crucial for enabling trust-minimized bridges to Bitcoin L2s.
BitVM2 and ColliderVM proposes mechanisms to circumvent these limitations and bring general-purpose computation to Bitcoin, enabling trust-minimized bridges without requiring a consensus fork. Though they share the same end goal, their approaches diverge significantly in architecture, assumptions, and trade-offs.
This article aims to present a high-level, dumbed-down overview on both protocols. For those of you with a more technical background, I will recommend directly reading from the water source — here are links to BitVM2 and ColliderVM papers.
How BitVM2 works
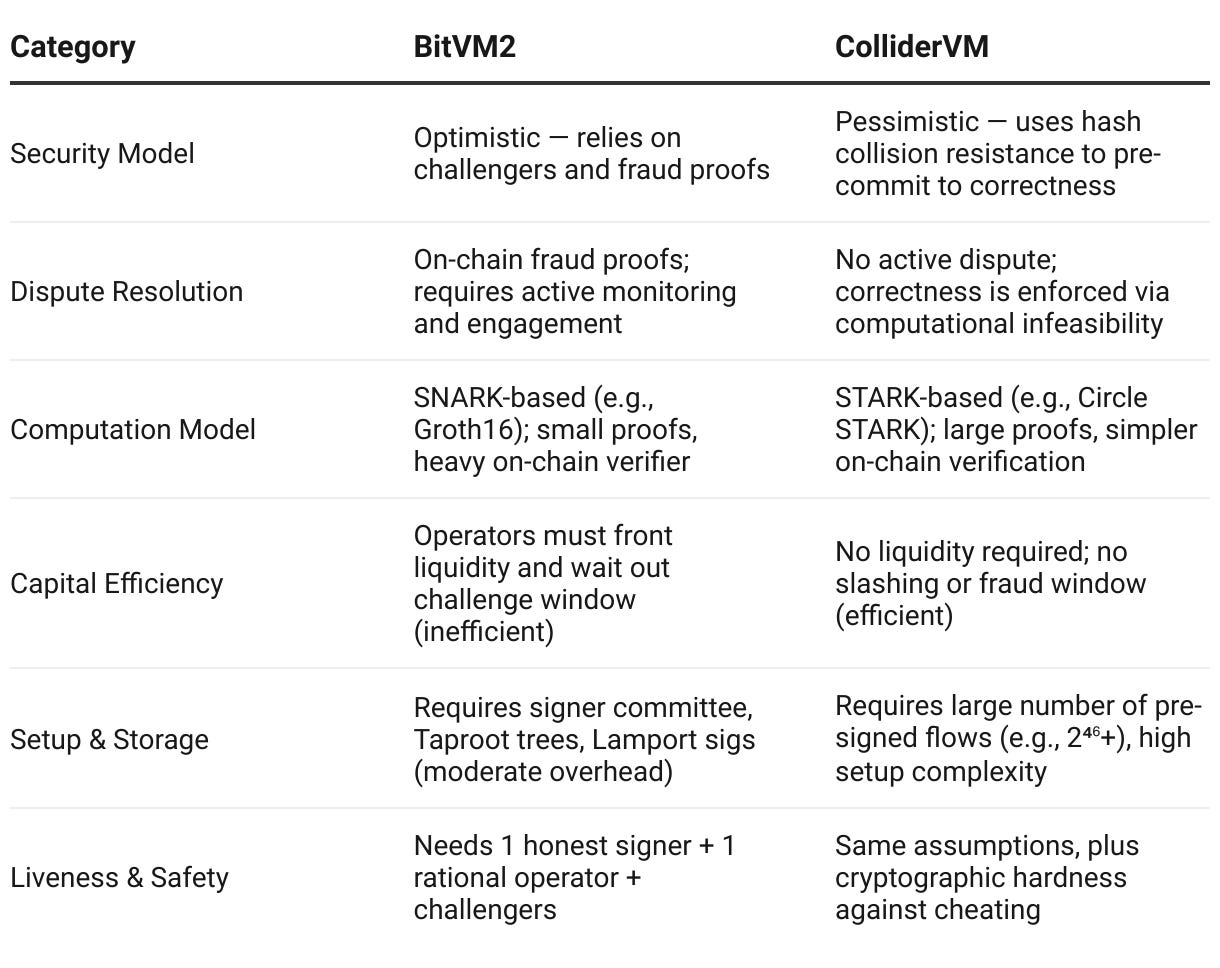
BitVM2 is a framework built around optimistic computation. The core idea is that computation is assumed to be honest unless proven otherwise (via fraud proofs). To achieve this, BitVM2 leverages SNARKs (succinct non-interactive arguments of knowledge), particularly Groth16, to verify arbitrary off-chain computations. However, since verifying a Groth16 SNARK on Bitcoin is too resource-intensive to fit in a single script (often gigabytes in size), BitVM2 splits the verifier into smaller sub-programs, each small enough to be executed within Bitcoin's transaction and block constraints.
In practice, an operator commits on-chain to the result of a computation (e.g., a bridge withdrawal). If no one challenges this claim, it goes through after the timeout window passes. But if someone does challenge, they must present a fraud proof, pinpointing the specific step in the computation that was falsified. This involves running that specific sub-program on-chain and showing that the claimed intermediate value is invalid. All of this can be resolved with just three on-chain transactions, making the system quite efficient compared to older fraud-proof designs like Truebit or the original BitVM.
The BitVM2 system depends on three key roles:
A committee of signers who enforce the transaction flow via pre-signed transactions (or future covenants).
Operators who execute the computation.
Challengers, anyone in the Bitcoin network who can verify and disprove dishonest computation.
As long as one signer is honest during setup, one operator is honest for liveness, and one rational challenger is active, the system is secure.
How ColliderVM works
ColliderVM, by contrast, takes a pessimistic route. It avoids fraud proofs entirely and instead uses a clever cryptographic commitment scheme based on hash collision resistance to ensure correct computation.
It builds on the ColliderScript concept but drastically improves its efficiency, reducing the number of required hash evaluations by over 10,000×. The essence of ColliderVM is this: A signer pre-signs a series of Bitcoin transactions that collectively represent the logic of a program, split into multiple subfunctions. Each flow enforces the order of operations (e.g., f₁ → f₂ → f₃) without being bound to a specific input value.
To ensure that the same input is used consistently throughout the flow (and to prevent cheating by providing different inputs to each step), ColliderVM uses a hash-commitment mechanism. The operator must find a nonce r such that H(x, r) maps to a pre-defined set D. If the operator tries to cheat by using inconsistent inputs, they would have to find a hash collision within D, a computationally intensive task that will be economically infeasible for anyone to attempt.
Take, for example, setting the parameters to L = 36 and B = 100. This requires 236 presigned flows; an honest operator needs to perform 64 bits of work to evaluate f, while a malicious operator needs 82. As mentioned, currently (April 2025) mining Bitcoin require 78 bits of work for which the miner gets 3.125 BTC.
Therefore, the attacker needs to spend work equivalent to around 50 BTC. The legitimate operator, at least for the hashing part, needs work that is ≈ 3.125/214 BTC, which represents ~262,144x less work than the attacker!
As such, ColliderVM does not require on-chain fraud proofs or slashing mechanisms. Security arises from cryptographic hardness assumptions, making the system more passive from a network perspective but also more front-loaded in setup complexity.
Which way, Bitcoin man?
BitVM2 is conceptually elegant and operationally proven in similar systems like Arbitrum and the OP Stack. It benefits from fast dispute resolution (3 transactions) and permissionless verification. But it depends on active monitoring, economic incentives for challengers, and the setup cost of handling large verifier scripts on Bitcoin — even in sub-program chunks. Moreover, the system remains capital inefficient, requiring operators to fund user withdrawals upfront while waiting out challenge windows.
On the other hand, ColliderVM has no fraud proof window, no need for economic incentives to challenge, and operators do not need to pre-fund withdrawals. This makes it more aligned with the more “traditional” beliefs of Bitcoiners — minimal trust, no long-running watchers, and no slashing. However, ColliderVM’s main challenge is in its setup scalability: generating and managing billions of pre-signed flows is a logistical and engineering hurdle. While this can be mitigated through improvements in tooling or parameter tuning, as of now it remains a considerable barrier to practical deployment — there is still not enough transactional demand on Bitcoin L2s to justify ColliderVM’s massive computational overhead per deposit or withdrawal on Bitcoin.
In the realm of trust-minimized Bitcoin bridges, BitVM2 is relatively more mature and may be easier to deploy in early designs — especially where challenger incentives and fraud windows are acceptable tradeoffs. ColliderVM, while still experimental, offers a compelling future path for "set-and-forget" secure computation on Bitcoin.
In the long run, ColliderVM’s model may be more aligned with Bitcoin’s ethos: trustless, final, and economically lean. But for immediate scalability, especially with existing SNARK ecosystems, BitVM2 may be the more practical short-term solution. The best design might even combine both — using BitVM2’s challenge mechanisms in early stages and evolving into ColliderVM-style enforcement as tooling and hardware capabilities mature.
Also published on X: https://x.com/delken_/status/1912138039867883849